WriteUp > HTB Sherlocks — MisCloud (Medium)

Scenario: My name is John. I am a student who started an e-commerce startup business named “DummyExample” with my partner, James. Initially, I was using WordPress and shared hosting. After experiencing good traffic, I decided to migrate from WordPress to a customized website on Google Cloud Platform (GCP). Currently, my partner and I are working on the website, contributing to a Gitea server hosted on GCP. I migrated all customer data to cloud storage. Recently, my data was breached, and I have no clue how it happened or what was vulnerable. My GCP infrastructure consists of five VM instances and a single Cloud Storage. There is one Windows machine for my partner to use, with very restricted permissions over GCP, only allowing access to his Gitea account. I have two Linux machines for my work, one for hosting the Gitea server and another for packet mirroring. All the machines have public IPs but very restricted access due to firewalls in place. Due to budget constraints, I can’t use the Google Security Command Center service, so I am providing you with the VPC network traffic capture and the Google Cloud logs.
Q1. What’s the private IP address of the Windows machine?
There are two approaches to solve this question
- Initial packet capture statistics and user agent strings (Basically elimination strategy)
- You will uncover it after some time as the lab proceeds
For first, I listed down the IP addresses involved using the statistics feature. From this I observed this:
10.128.0.3
10.128.0.4 (34.66.191.87 — gitea server[public IP] > from Hostname)
10.128.0.7
From VT
169.150.196.101 — attacker IP
This means that 10. subnet is private IP addresses of the machines and 34. are public IP addressesNow, just filter the IP addresses and observe the user agent strings, for the IPs
I will reference the second strategy going ahead.
Q2. Which CVE was exploited by the threat actor?
Since the gitea server was public facing my initial doubt went ahead towards web-application has been exploited to get the Initial Access. I filtered the traffic with HTTP and observed POST requests. One of the post requests had suspicious content

decoding the base64 code

A reverse shell!! on port 14509, which clearly means Remote Code execution vulnerability. Now just research the web for RCE Gitea, there are multiple but from the response packets we can get the server version that is vulnerable!

Going ahead I then filtered the traffic with port 14509 and followed the TCP stream


Then in this stream, I got the second strategy for Q1, attacker enumerated compute instances on the server.

Q3. What is the hostname and port number to which the reverse shell was connecting?
refer above!
Q4. From which IP address was the CVE exploited, and is this threat an insider or outsider attack?
Looking at the source IP, its clear that the internal machine was used.
Q5. Which account helped the threat actor to pivot?
From the TCP stream, I saw the attacker used a service account that TA enumerated using the command “gcloud auth list”. The service account mentioned isthe default service account created when a compute instance is created.

Q6. Which machines did the threat actor log into? (sorted alphabetically)
From the TCP stream at the end attacker created SSH keys, to follow this I assumed attacker used SSH to move laterally to other machines, hence I filtered the packet with IP address of the gitea server and ssh protocol


I then noted which public IP addresses from the GCP instances are involved. referencing these.
Q7. What’s the original name of the sensitive file?
Moving on with GCP logs that are provided, it was quite straight forward by examining the caller IP and resource viewed

Q8. Which gcloud role did the threat actor try to assign to the storage bucket to make it publicly accessible?

Attacker add a role called storage.legacyObjectReader and assigned it to all Users
Q9. Which account led to the cloud storage data breach?

Q10. Which port number was exploited by the attacker to exfiltrate data that is allowed by default ingress traffic rules in the default VPC network?
The traffic involved to and from traffic from internal IP to external IP including a critical file mentioning cusdata.xlsx.enc, which leads to potential exfiltration attempt.
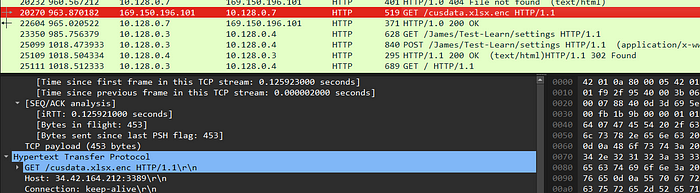
Q11. What is the key to decrypt the encrypted file?
Since we saw a HTTP post request has been used to transfer this file, lets see the bytes transferred using TCP


Follow the TCP stream right after the post request.

You will see a repeating string of l33t speak characters, that immediately raises eyebrows. After some trial and error and context information (James machine), I found the right key used.
Q12. What are the SSN and credit card numbers of “Founder John”?
Lets get the encrypted file

In the traffic another python script was requested from TA’s C2 server

Lets analyse the script

The code basically XORs the data using password provided (the one which we found out) and saves the file. To get the decrypted data we basically need to use the same strategy since its XOR.


Q13. Which Google Cloud service is an alternative to Gitea?

Q14. Is it safe to use the Default Compute Engine Service Account on VM instances?
No default accounts are ever safe to use due to privileges they provide!
Q15. Which Google Cloud service restricts data exfiltration from Cloud Storage?

Challenge Link:https://app.hackthebox.com/sherlocks/MisCloud
