WriteUp > HTB Sherlocks — APTNightmare

Difficulty Level: Medium
Scenario: We neglected to prioritize the robust security of our network and servers, and as a result, both our organization and our customers have fallen victim to a cyber attack. The origin and methods of this breach remain unknown. Numerous suspicious emails have been detected. In our pursuit of resolution, As an expert forensics investigator, you must be able to help us.
Q1. What is the IP address of the infected web server?
Q2. What is the IP address of the Attacker?
Filter the packet to HTTP, you will see mostly two IPs, from request-response its clear which one is web server and which one is the attacker IP

Q3. How many open ports were discovered by the attacker?
To solve this, one should know how port discovery works. When a TCP connect scan is in progress, the port, when open, will send an acknowledgement; if it's closed, it won't. So we need to filter out packets with the ACK flag set as 1 and Seq=1 and Ack=1. This will give us the packets returned where ports are open!

Q4. What are the first five ports identified by the attacker in numerical order during the enumeration phase, not considering the sequence of their discovery?
From the list of ports sort them numerically
Q5. The attacker exploited a misconfiguration allowing them to enumerate all subdomains. This misconfiguration is commonly referred to as (e.g, Unrestricted Access Controls)?
I filtered the pcap with only DNS, for our interests in source and destination, we had only two packets with query type as AXFR. AXFR basically is a protocol used to replicate a DNS database into other DNS servers for backup, this can be maliciously used by attackers to enumerate the domain.
Q6. How many subdomains were discovered by the attacker?
IF we check the response packet we can see the list of sub-domains.


Q7. What is the compromised subdomain (e.g., dev.example.com) ?
Moving on to the HTTP filter, if we go down, we will see a lot of POST requests to the page index.php in any one of the packet if we take a look at the host section we will see the sub-domain that has been targetted.

Q.8 What email address and password were used to log in?
Looking at the packets it looks like there is some kind of brute force attempts where multiple POST requests on index.php, but if it is successful login attempt, the next immediate packet will be a different one may be a different page.

I did see such behaviour where after too many POST requests, there is one that redirected to dashboard.php
Checking the POST request packet we will find the credentials used by following the HTTP stream on the packet prior to it.

Q9. What command gave the attacker their initial access ?
We also see some POST requests on page dashboard.php, of the the POST data contains a script

|mkfifo /tmp/mypipe; cat /tmp/mypipe | /bin/bash | nc -l -p 5555 > /tmp/mypipeThe script creates a named pipe (mypipe) in the temp directory (named pipes are used for interprocess communication). The next command cat /tmp/mypipe will read the data in the pipe (in this case its the command that the attacker sent) and this command will then be passed on to the /bin/bash (command shell). Lastly, the output of the command will be again added into named pipe for the attacker to receive.
Q10. What is the CVE identifier for the vulnerability that the attacker exploited to achieve privilege escalation?
Now we know that the attacker is listening on port 5555, so there is some kind of communication going on between the attacker and the infected host through port 5555.
Filtering the traffic to tcp.port == 5555 we can see this communication

Following the TCP stream after three way handshake

if we scroll down we will see a shell file called pwnkit.sh

After googling this file we will get this answer, its basically a payload that exploits linux local privilege escalation vulnerability

Q.11 What is the MITRE ID of the technique used by the attacker to achieve persistence (e.g, T1098.001)?
Going further down the stream we can see the attacker abused crontab to schedule a cronjob, mostly used for persistence in linux systems

Q12. The attacker tampered with the software hosted on the ‘download’ subdomain with the intent of gaining access to end-users. What is the Mitre ATT&CK technique ID for this attack?

The attacker here deployed a file called cs-windows.exe from own infrastructure to target infrastructure. This activity can be classified as Supply-Chain attack where attacker places malicious executables that will be potentially downloaded by mass customers.
Q13. What command provided persistence in the cs-linux.deb file?
To find this firstly we need to export this cs-linux.deb file from the packet capture

Moving ahead we can use the linux program called MC which is used to extract deb package contents using dpkg used to manage debian packages

We now have the py file cs-linux, lets analyse the code in it.

After decoding the base64 code in cyberchef

we see a command echo cs-linux && >> ~/.bashrc. The ~/.bashrc file is a shell script that is executed every time a user opens a new terminal session or logs into the system.
Q14. We received a phishing email can you provide subject of the email ?
We have the memory image of the machine, we can look for strings in that. I searched for “Subject” to get the desired results

Q5. What is the name of the malicious attachment?
Using similar technique we can search for key words like attachment, doc, pdf, zip. My suspicious was more towards doc files hence searched for doc

Q17. Please identify the usernames of the CEOs who received the attachment.
Keyword search “From:”

Q18. What is the hostname for the compromised CEO?
We have been provided with the Kape files, which contains a log file. In this log file all details of the host are mentioned

Q19. What is the full path for the malicious attachment?
From the KAPE file, we can use $MFT which has the file structure and upload this in MFT explorer, after searching for files I located the file in Downloads folder
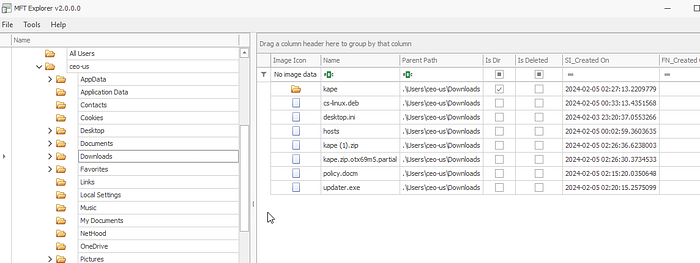
Q20. Can you provide the command used to gain initial access?
For this I searched for Powershell.evtx since I assumed there should be some kind of powershell script executed on the machine. We can get the powershell.evtx through Kape files

Q21. Provide a Popular threat label for the malicious executable used to gain initial access?
From the above script we can conclude there is communication on port 806 to get a file named a following a TCP stream on port 806 we get another encoded powershell code

decoding this and saving the file from cyberchef we get the executable which we can upload it on the VirusTotal

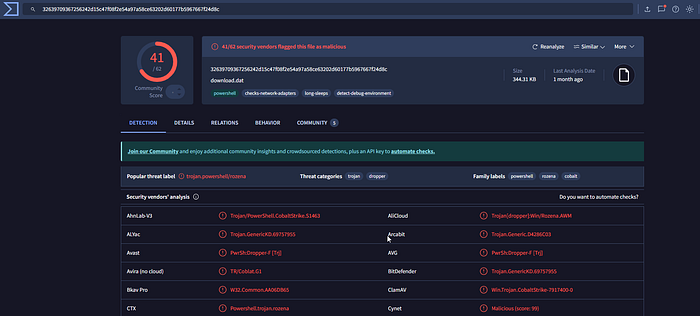
Q22. What is the payload type?
From the hint provided we can use 1768.py which is program use to determine the type of payload
execute command python3 1768.py -r download.exe

Q23. What is task name has been add by attacker?
From the KAPE files again we can look for Tasks folder to determine the Task added.

Challenge Link: https://app.hackthebox.com/sherlocks/APTNightmare







![[HackTheBox Sherlocks Write-up] APTNightmare](https://miro.medium.com/v2/resize:fit:679/0*89pSBL9Vbc5lM1Ve.png)

![HTB Loggy Active | [Easy] : Loggy](https://miro.medium.com/v2/resize:fit:679/1*Cv6V-om5U8IjjX2oqtuRUg.png)